Companies no longer rely on paper documents. The entire documentation process has become digital. Digital signature allows you to add signatures on your digital documents, thereby ensuring that they are equally credible and carry the same legal importance as paper documents
How do Digital Signatures work?
The Digital Signatures require a key pair (asymmetric key pairs, mathematically related large numbers) called the Public and Private Keys. Just as physical keys are used for locking and unlocking, in cryptography, the equivalent functions are encryption and decryption. The private key is kept confidential with the owner usually on a secure media like crypto smart card or crypto token. The public key is shared with everyone. Information encrypted by a private key can only be decrypted using the corresponding public key.
In order to digitally sign an electronic document, the sender uses his/her Private Key. In order to verify the digital signature, the recipient uses the sender’s Public Key.
Let us understand how the Digital Signatures work based on an example. Assume you are going to send the draft of a contract to your lawyer in another town. You want to give your lawyer the assurance that it was unchanged from what you had sent and that it is really from you.
- You copy-and-paste the contract into an e-mail note. Get electronic form of a document ( eg : – word or pdf file)
- Using special software, you obtain a message hash (fixed size bit string) of the contract.
- You then use your private key to encrypt the hash.
- The encrypted hash becomes your digital signature of the contract and is appended to the contract.
At the other end, your lawyer receives the message.
- To make sure the contract is intact and from you, your lawyer generates a hash of the received contract.
- Your lawyer then uses your public key to decrypt the Digital Signature received with the contract.
- If the hash generated from the Digital Signature matches the one generated in Step 1, the integrity of the received contract is verified
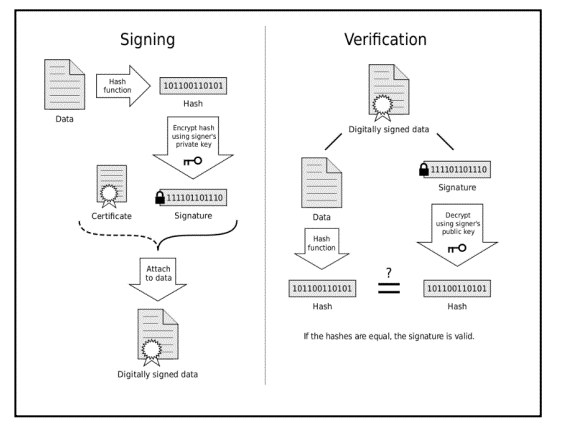
Figure: How Digital Signatures ensure Authenticity, Integrity and Non- Repudiability of the Contract (Source – Wikipedia)
Note: Message digest, also known as the hash of a message, is a small piece of data that results by applying a particular mathematical calculation (hashing function) on the message. Two properties of message digests to note: (i) a small alteration in the original message would cause a big change in the message digest; (ii)derivation of the original message is not possible from the message digest.
The hash produced from these functions is a fixed length bit string. For example: – The widely used message digest function SHA -1 generates a 160 bit hash whereas the SHA-2 function generates 256 bit hash as output. The usage of MD5 is to be discontinued by the Certifying Authorities as per the Amendment to the Rules of the IT Act published in 2009.(Link on the CCA website – //cca.gov.in/rw/pages/rules.en.do
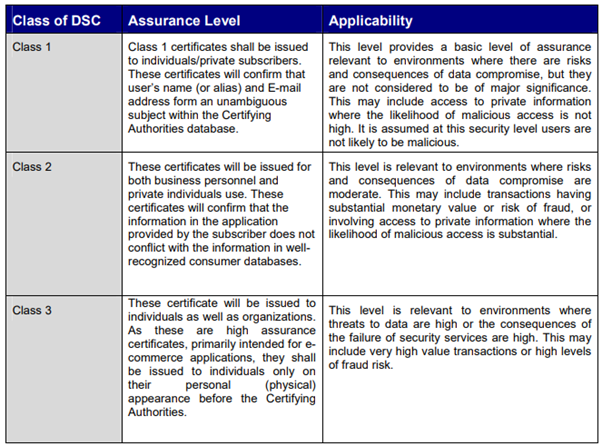
Classes of Digital Signature Certificates
Depending upon the requirement of assurance level and usage of DSC the following are the classes of Digital Signature Certificates
What is Cryptography?
Cryptography is the science of enabling secure communications between the sender and one or more recipients. This is achieved by the sender scrambling a message (with a computer program and a secret key) and leaving the recipient to unscramble the message (with the same computer program and a key, which may or may not be the same as the sender’s key).
There are two types of cryptography: Secret/Symmetric Key Cryptography and Public Key Cryptography.
Secret key (symmetric/conventional) cryptography – is a system based on the sender and receiver of a message knowing and using the same secret key to encrypt and decrypt their messages. One weakness of this system is that the sender and receiver must trust some communication channels to transmit the secret key to prevent from disclosure. This form of cryptography ensures data integrity, data authentication and confidentiality.
Public key (asymmetric) cryptography – is a system based on pairs of keys called the public key and private key. The public key is published to everyone while the private key is kept secret with the owner. The need for a sender and a receiver to share a secret key and trust some communication channels is eliminated. This concept was introduced in 1976 by Whitfield Diffie and Martin Hellman.
The Digital Signatures created using the private key ensures data integrity, data authentication and nonrepudiation. However, to ensure confidentiality, encryption of the data has to be done with the recipient’s public key.
CCA Explained
As per Section 18 of The Information Technology Act, 2000 provides the required legal sanctity to the digital signatures based on asymmetric cryptosystems. The digital signatures are now accepted at par with handwritten signatures and the electronic documents that have been digitally signed are treated at par with paper documents.
The IT Act provides for the Controller of Certifying Authorities(CCA) to license and regulate the working of Certifying Authorities. The Certifying Authorities (CAs) issue digital signature certificates for the electronic authentication of users.
The Controller of Certifying Authorities (CCA) has been appointed by the Central Government under section 17 of the Act for purposes of the IT Act. The Office of the CCA came into existence on November 1, 2000. It aims at promoting the growth of E-Commerce and E-Governance through the wide use of digital signatures.
The Controller of Certifying Authorities (CCA) has established the Root Certifying Authority (RCAI) of India under section 18(b) of the IT Act to digitally sign the public keys of Certifying Authorities (CA) in the country. The RCAI is operated as per the standards laid down under the Act.
The CCA certifies the public keys of CAs using its own private key, which enables users in the cyberspace to verify that a given certificate is issued by a licensed CA. For this purpose it operates, the Root Certifying Authority of India(RCAI). The CCA also maintains the Repository of Digital Certificates, which contains all the certificates issued to the CAs in the country.
Digital Signature Certificate Verification
Digital Signature Certificates are verified using a Chain of trust. The trust anchor for the Digital Certificate is the Root Certifying Authority (CCA in India). A root certificate is the top-most certificate of the hierarchy, the private key of which is used to “sign” other certificates. All certificates immediately below the root certificate inherit the trustworthiness of the root certificate. Certificates further down the tree also depend on the trustworthiness of the intermediates (often known as “subordinate certification authorities”). The Digital Certificate verification process is a recursive process in which the program verifying the end user certificate verifies the validity of the certificate of the issuing authority until it finds a valid certificate of a trusted party. On successful verification of the trusted party Certificate, the Digital Certificate verification stops. In case a trusted party Certificate is not found by the program, the Digital Certificate verification process ends in failure.
PROCUREMENT OF DIGITAL SIGNATURE CERTIFICATES
The applicant for the Certificate must generate his/her own key pair and send the public key to the CA with some proof of his/her identity. The CA will issue a Digital Signature Certificate containing the public key. The CA will digitally sign the certificate using its private key and then send the certificate to the applicant. The CA will check the applicant’s identification before it generates the certificate and signs the request. Different Certifying Authorities may issue certificates with varying levels of identification requirements. One CA may insist on seeing the Identity card while another may want a signed letter authorizing certification from anyone requesting a certificate.
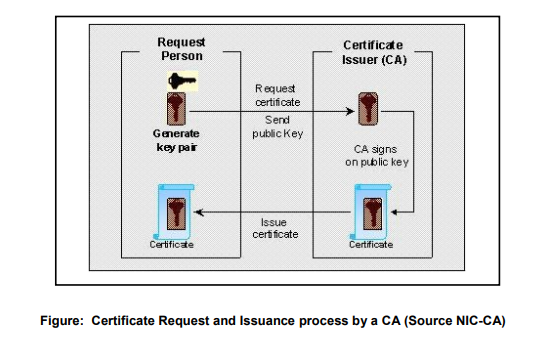
Procedure for procuring Digital Signature Certificates The CCA has licensed seven Certifying Authorities in India to issue Digital Signature Certificates to the end users. The National Informatics Centre issues Digital Signature Certificates primarily to the Government/ PSU’s and Statutory bodies. The Institute for Development of Research in Banking Technology (IDRBT) issues Digital Signature Certificates primarily to the banking and financial sector in India. The remaining five CAs – Safescrypt, TCS, MTNL, n(Code) Solutions and eMudhra issue Digital Signature Certificates to all end users across all domains. More than 16 lakh Digital Signature Certificates have been issued by the different CA’s in our country at the time of publication of this document.
Precautions while using Digital Signature Certificates
Digital Signatures are legally admissible in the Court of Law, as provided under the provisions of IT Act 2000. Therefore users should ensure that the Private keys are not disclosed to anyone. For example:- Users generally give their crypto tokes to their personal secretaries or subordinates to sign the documents on their behalf. Any illegal electronic transaction undertaken using a person’s private key cannot be repudiated by the certificate owner and will be punishable in the Court of Law.
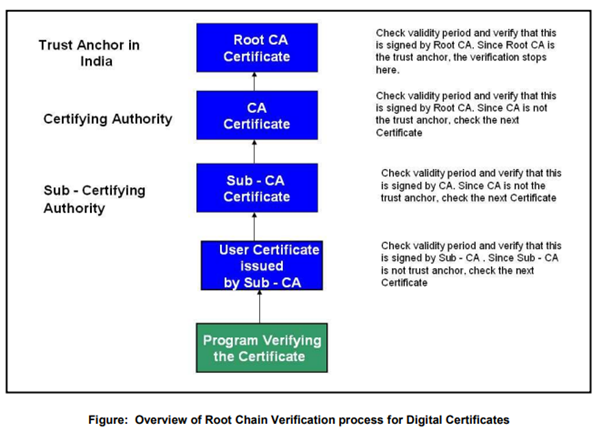
The e-Governance applications should also undertake Root chain verification and CRL verification in addition to the Public Key verification while doing the Digital Signature verification.
Electronic Signature Laws & Regulations – India
The use of electronic signatures in electronic contracts is on the rise in India, due in part to the government’s Digital India initiative which focuses on enhancing digital infrastructure and on transforming India into a paperless economy. Companies doing business in India are also increasingly utilizing electronic signatures to complete their transactions.
In India, electronic and certificate-based digital signatures are regulated by the Information Technology Act, 2000 (IT Act) and the following rules made under this Act:
Information Technology (Certifying Authorities) Rules, 2000;
· Digital Signature (End Entity) Rules, 2015; and
· Information Technology (Use of Electronic Records and Digital Signature) Rules, 2004.
The IT Act distinguishes between electronic signatures and certificate-based digital signatures, but both have the same status as handwritten signatures under Indian law. Digital signatures are preferred for certain government transactions such as e-filing with the Ministry of Corporate Affairs, and goods and service tax filings.
Valid electronic signatures must include an electronic authentication technique or procedure specified in the Second Schedule of the IT Act. The Second Schedule currently specifies the following e-KYC (Know Your Customer) authentication techniques and procedures:
The IT Act distinguishes between electronic signatures and certificate-based digital signatures, but both have the same status as handwritten signatures under Indian law. Digital signatures are preferred for certain government transactions such as e-filing with the Ministry of Corporate Affairs, and goods and service tax filings.
Valid electronic signatures must include an electronic authentication technique or procedure specified in the Second Schedule of the IT Act. The Second Schedule currently specifies the following e-KYC (Know Your Customer) authentication techniques and procedures:
- 1. Aadhaar e-KYC (see below for additional details);
- 2. Other e-KYC services (e.g. e-KYC using Permanent Account Number (PAN)).
Under Indian law, reliable electronic and digital signatures carry a presumption of validity compared to other “non-recognized” electronic signatures. However, in common with other jurisdictions, Indian law will not consider an agreement invalid solely on the grounds that it was formed with such non-recognised electronic signatures.
For an electronic signature to be considered reliable and presumptively valid under the IT Act:
- 1. It must be unique to the signatory;
- 2. at the time of signing, the signatory must have control over the data used to generate the electronic signature;
- 3. any alteration to the affixed electronic signature, or to the document to which the signature is affixed, must be detectable;
- 4. there should be an audit trail of steps taken during the signing process; and
- 5. The signer certificates must be issued by a certifying authority (CA) recognized by the Controller of Certifying Authorities appointed under the IT Act. A list of licensed CAs is available at //www.cca.gov.in/licensed_ca.html.
Note:
For e-signing processes initiated in India, Adobe applies an electronic seal using digital certificates from eMudhra, which are recognized under the IT Act and thus carry the presumption of validity for the completed agreement.
Judges and magistrates are familiar with the law concerning e-signatures and e-contracts, although some local authorities insist on physical documents for keeping registers and records under statutes, and on the use of traditional “wet signatures” for authentication.
Special considerations
Aadhaar e-KYC
Using Aadhaar e-KYC as an e-authentication technique requires verification of the signatory’s identity using his or her Aadhaar number. According to the Aadhaar and Other Laws (Amendment) Act, 2019, an entity may be allowed to perform Aadhaar authentication, with the voluntary consent of the Aadhaar number holder, only if the UIDAI (Unique Identification Authority of India) is satisfied that the requesting entity is:
- compliant with such standards of privacy and security as may be specified by regulations; and
- permitted to offer authentication services under the provisions of any other law made by Parliament.
Accordingly, authentication using Aadhaar e-KYC services is currently only being offered to private application service providers (ASPs) by the following two government entities:
- National Securities Depository Limited (NSDL); and
- Centre for Development of Advanced Computing (C-DAC)
Note:
Adobe has partnered with NDSL to provide Aadhaar e-KYC services to our customers worldwide. For more information, please see https://helpx.adobe.com/sign/using/adobesign-idp-aadhaar.html
Indian Stamp Act
The Indian Stamp Act, 1899, requires that certain documents be stamped at or before the time of execution. Currently no laws in India prescribe a method for stamping electronic documents. Some states such as Maharashtra, Karnataka and Delhi specifically extend the requirement for stamping to electronic records. When stamps are accepted electronically, solutions like Adobe Sign can be tailored to meet those requirements.
Companies should always confirm with their internal legal team whether a document needs to be stamped before signing and executing the document electronically. If a document is signed and executed electronically and is required to be stamped, then the company should ensure that a physical copy of the document is prepared and stamped. If a document is not properly stamped, then penalties may be imposed.
Use cases that require a traditional signature
The IT Act allows the use of an electronic or digital signature for (i) filing any form, application or document with any government authority; (ii) issue of any license, permit or approval by the government authority; and (iii) receipt or payment of money in a particular manner, in electronic form. The government authority may create rules prescribing the manner in which electronic records and electronic signatures are accepted for these purposes. For instance, Rule 7 of the Companies (Registration Offices and Fees) Rules, 2014 specifies that every application, financial statement, prospectus, return, declaration, memorandum, articles, particulars of charges, or any other particulars or document or any notice, shall be filed in computer readable electronic form in pdf. Further, Rule 8 stipulates that an e-form must be authenticated using Digital Signature; and the Central Board of Direct Taxes have notified procedure for filing e-TDS/ e-TCS and other forms using digital signatures.
In addition, certain government authorities have initiated e-filing regimes and permit electronic signatures for the following purposes:
- Digital locker self-attestation;
- Goods and sales tax returns and invoices;
- Account opening in banks and post offices;
- Application for driving license renewal and vehicle registration;
- Application for birth, caste, marriage and income certificate etc.;
- Passport application for issuance or reissue/renewal;
- Telecom application for new connection.
Electronic contract formation methods such as click-wrap, non-CA issued certificates etc. are not explicitly recognized under the IT Act but may be used for e-contract formation. Under Section 10-A of the IT Act, the formation of an agreement by electronic means would not be held invalid solely on the ground that the agreement was formed electronically. However, such non-recognized electronic signatures do not have the presumption of validity of electronic signatures and the validity of electronic contracts signed using such electronic signatures may be disputed. In such a case, the signatory may be required to prove:
- the generated signature can be linked only to the signatory and to no other person;
- only the signatory had access to and control over the document at the time of signing;
- any alteration to the signature or the information made after the signature is affixed is detectable; and
- the essentials of a valid contract under the Indian Contract Act, 1872, such as offer, acceptance and intention to create a legal relationship, the capability of the parties, consideration etc., are met.
The conduct of the parties with respect to the subject matter of the contract/electronic record may also be relevant in this context.
Transacting with public sector entities
Under Indian law, the following documents must be signed with a traditional wet signature:
- A negotiable instrument (other than a cheque) as defined in section 13 of the Negotiable Instruments Act, 1881. A negotiable instrument includes a promissory note, bill of exchange or a cheque.
- A power-of-attorney as defined in section 1-A of the Power-of-Attorney, Act, 1882.
- A trust as defined in section 3 of the Indian Trusts Act, 1882.
- A will as defined in section 2(h) of the Indian Succession Act, 1925, including any other testamentary disposition.
- Any contract for sale or conveyance of immovable property or any interest in such property.
In addition, notarization is carried out by a registered notary under his or her signature and seal. As a matter of practice, this has always been carried out through a physical seal and wet signature and requires verification of physical copies of documents.
Note:
Disclaimer: Information on this page is intended to help businesses understand the legal framework of electronic signatures. However, Adobe cannot provide legal advice. You should consult an attorney regarding your specific legal questions. Laws and regulations change frequently, and this information may not be current or accurate. To the maximum extent permitted by law, Adobe provides this material on an “as-is” basis. Adobe disclaims and makes no representation or warranty of any kind with respect to this material, express, implied or statutory, including representations, guarantees or warranties of merchantability, fitness for a particular purpose, or accuracy.
Share this Post











